Site to Site VPN with two Tomato based Routers
Recently I was bit by a setup on a site I manage where two Tomato based routers talk to each other on a TUN and TAP connection. One of the routers configs got corrupted in a power outage and my backup was corrupt as well. This left me with a lack of documentation on how to recover. This is my copy of my configuration so that both you and I can setup two Tomato based routers to have a VPN between them.
Credit: I owe Steve a great bit of credit from the URL below. Thank you!
Update: 20200501 : This was updated slightly to reflect some of the changes from Fresh Tomato (2020.2)
The Server
This is the key configuration. I recommend not starting the VPN with WAN until you get it right. So uncheck that. For the Keys, see the link above.
TUN based setup (routed)
TAP (bridge) based setup
The Client
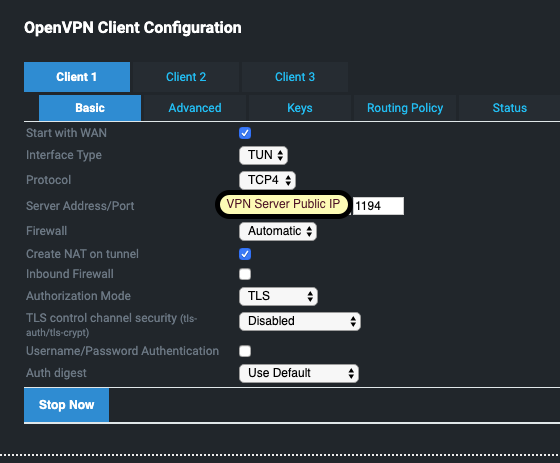
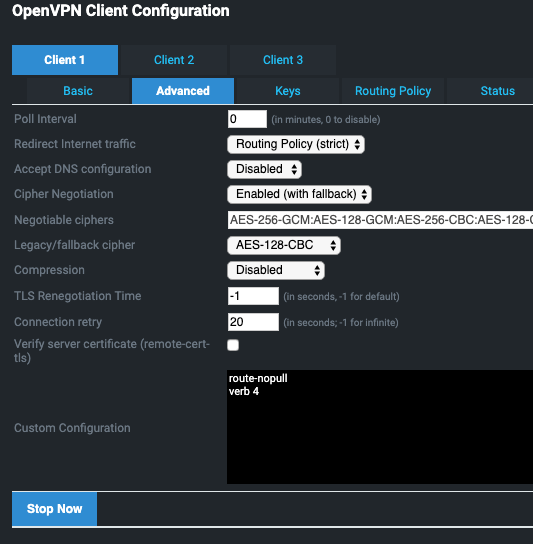
TUN routed VPN (layer 3+)
The client configuration needs to match the servers in terms of ciphers and compression. My settings are shown below, but you may be able to adjust yours to match TCP vs UDP and compression types. Remember to make sure your routes allow you to route traffic to your remote's LAN network (a TUN VPN) and not the VPN network which will be a different IP address. The goal is to get the IPs on your client normal LAN to talk to systems on your remote LAN, not on the VPN network point to point between the routers.
 |
| (optional)TomatoUSB client advanced |
This is what your connection will look like if it is configured correctly from the client side, you will see TUN data and TCP data in both directions.
TAP Ethernet Bridge
This method extends the ethernet network between locations across a VPN connection. This will make your IP space the same and allow you to use the DHCP server on both networks. Be careful, as this will create a common collision domain, and allow multicast and if you are not careful really mess up your network. Do not set the VPN to start on boot until you know it works, so you can restart your router on either side if something gets borked. This setup is the same as the setup for the TUN configuration above, except the first page. I used the same certificates for both.
Separate WIFI w/ TAP
Creating a virtual Wifi and VLAN on your client to allow you to have a bridge AND a TUN vpn
coming soon.